Block Ciphers
Topics
A block cipher is a symmetric key encryption scheme (SKES) in which a fixed-length block of plaintext determines an equal-sized block of ciphertext.
Desired Properties of Block Ciphers (by Claude Shannon, 1949)
- Security:
- Diffusion: Each ciphertext bit should depend on all plaintext and all key bits.
- Confusion: The relationship between key bits, plaintext bits, and ciphertext bits should be complicated.
- Cascade / Avalanche Effect: Changing one bit of plaintext or key should change each bit of ciphertext with a probability of about 50%.
- Key Length: Should be small but large enough to preclude exhaustive key search.
- Efficiency:
- Simplicity: Easy to implement and analyze.
- High Encryption and Decryption Rate: Fast processing of data.
- Suitability for Software/Hardware: Versatile implementation options.
Advanced Encryption Standard
- AES is an SPN where the permutation operation consists of two linear transformations.
- All operations are byte oriented.
- The block size is 128 bites
- Each round key is 128 bites
- A key schedule is used to generate the round keys
- AES accepts three different key lengths (128, 192, 256 bits)
- 128 bits -> 10 rounds
- 192 bits -> 12 rounds
- 256 bits -> 14 rounds
General Structure
- The substitution operation (S-Box) is the only non-linear component of the cipher.
- The permutation operations spread out the non-linearities in each round.
Round Operation
- Each round updates a variable called State which consists of a 4x4 array of bytes (4*4*8=128 bits)
- State is initialized with the 128-bit plaintext
- After h rounds are completed, one final additional round key is XORed with State to produce the ciphertext (key whitening)
- AES round function uses four operations:
- AddRoundKey (key mixing)
- SubBytes (S-Box)
- ShiftRows (permutation)
- MixColumns (matrix mult./linear transformation)
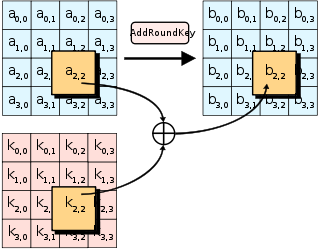
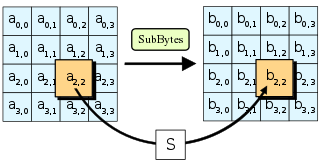
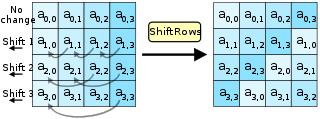
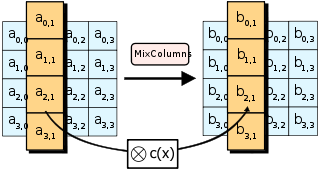
AES Encryption
- From the key k, derive h+1 round keys k0, k1, ..., kh via the key schedule.
- Encryption function proceeds as: State ← plaintext
for i = 1, 2, ..., h-1:
State ← State ⊕ ki-1
State ← SubBytes(State)
State ← ShiftRows(State)
State ← MixColumns(State)
State ← State ⊕ kh-1
State ← SubBytes(State)
State ← ShiftRows(State)
State ← State ⊕ kh
ciphertext ← State
Note: In the final round, MixColumns is not applied and XORed with kh (key whitening).
AES Key Schedule (for 128-bit keys)
- For 128-bit keys, AES has ten rounds, so we need eleven subkeys (last one for key whitening).
- Each ki is a 32-bit word
- Each group of 4 ki's forms a 128-bit subkey.
- The first round subkey (k0, k1, k2, k3) equals the actual AES key.
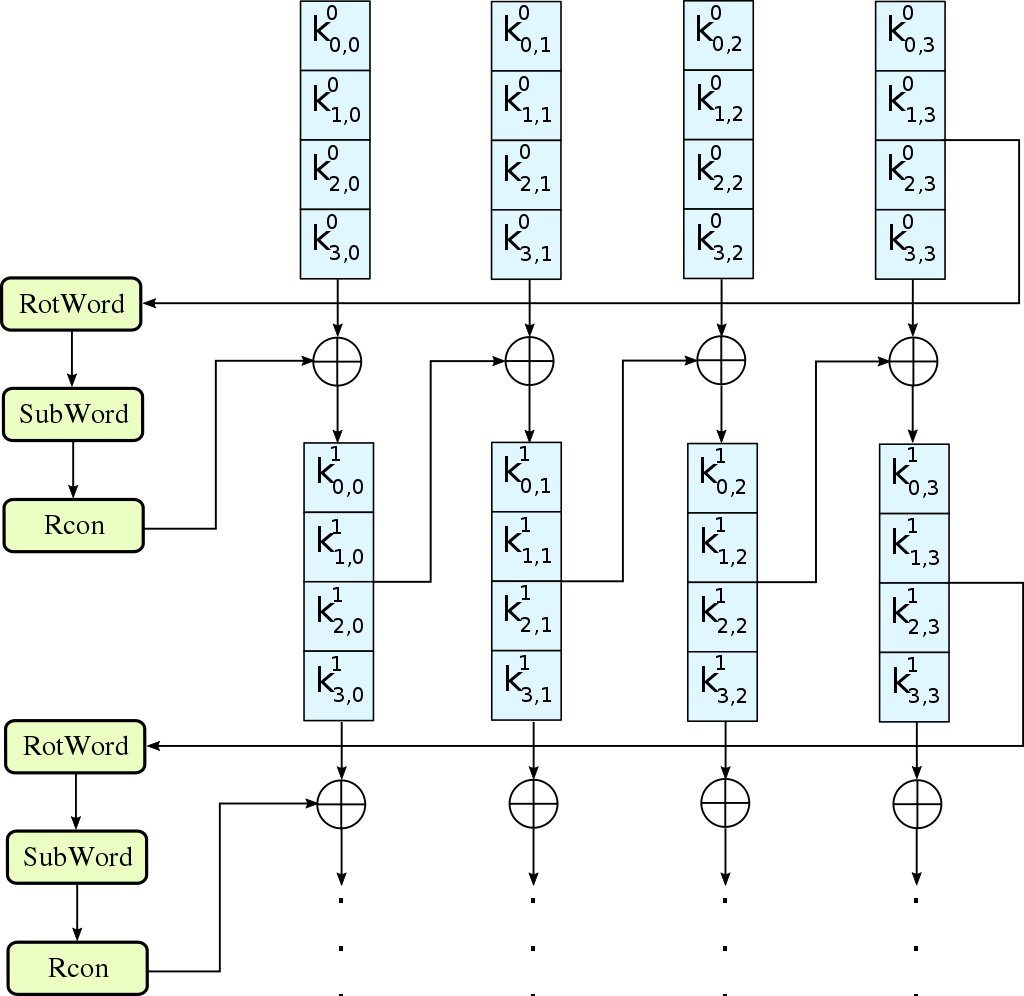
- The function fi:{0,1}32→ {0,1}32 are defined as follow:
- Left Shift the input cyclically by 8 bits. (RotWord)
- Apply the AES S-box to each byte. (SubWord)
- Bitwise XOR the left-most byte with a constant (Rcon) which varies by round accodring to the following table:
| Round | Constant | Round | Constant |
|---|---|---|---|
| 1 | 0x01 | 6 | 0x20 |
| 2 | 0x02 | 7 | 0x40 |
| 3 | 0x04 | 8 | 0x80 |
| 4 | 0x08 | 9 | 0x1b |
| 5 | 0x10 | 10 | 0x36 |
Data Encryption Standard
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST). DES was widely used in the 1970s and 1980s but has since been replaced by more secure algorithms like AES due to its shorter key length and vulnerability to brute-force attacks.
Structure of DES
Block cipher with 64-bit blocks, 56-bit key and 16 rounds:
Plaintext (64 bits)→ Initial Permutation
→ Feistel Network (16 rounds) with 56-bit key from Key Schedule
→ Inverse of Initial Permutation
→ Ciphertext (64 bits)
Feistel Network
Components of a Feistel Cipher
- Parameters: n (half the block length), h (# of rounds), l (key size)
- C = M = {0,1}2n, K = {0,1}l
- Key scheduling algorithm to determine subkeys from given key.
- Each subkey defines a component function Fi: {0,1}l x {0,1}n → {0,1}n
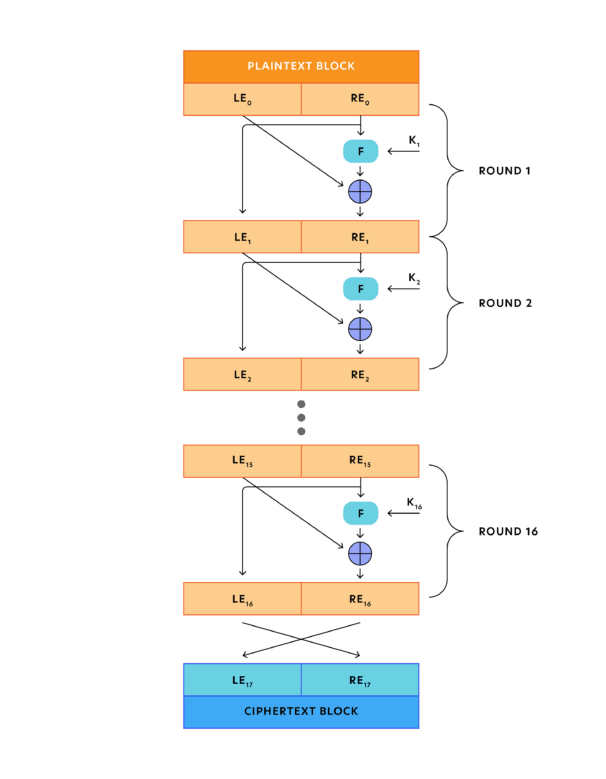
Design of the Feistel Network
- Plaintext is divided into two halves (LE0, RE0)
- Key is used to generate subkeys k1,k2,...,kh.
- F is a component function whose output is depending on REi and ki.
Notes on Feistel Cipher
- No restrictions on F in order for the encryption to be invert.
- Underlying Principle: Take something 'simple' and use it several times; hope that the result is complicated.
- Implementation:
- Encryption: One round implementation is enough. The same code can be used for each round.
- Decryption: Use the same code as encryption.
DES Encryption and Decryption
Encryption (with h rounds):- Plaintext m = (m0, m1) (= LE0, RE0)
- Round 1: (m0, m1) → (m1, m2); where m2 = m0 ⊕ F(k1, m1)
- Round 2: (m1, m2) → (m2, m3); where m3 = m1 ⊕ F(k2, m2)
- ...
- Round h: (mh-1, mh) → (mh, mh+1); where mh+1 = mh-1 ⊕ F(kh, mh)
- Ciphertext c = (mh, mh+1)
- Given c = (mh, mh+1) and k:
- mh-1 = mh+1 ⊕ F(kh, mh)
- ...
- m0 = m2 ⊕ F(k1, m1)
- m = (m0, m1)
Structure of the Component Function
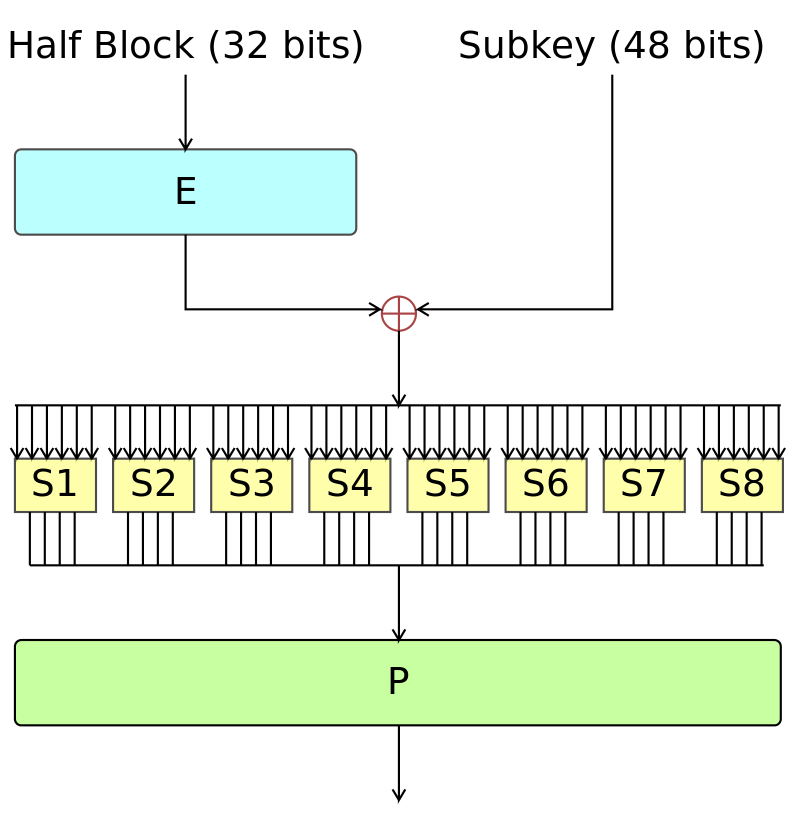
- E:{0,1}32 → {0,1}48 is an expansion table where it takes 32-bit block (mi) and returns 48-bit word.
- The S-box S:{0,1}6 → {0,1}4 takes 6-bit word and returns 4-bit word.
- The permutation P:{0,1}32 → {0,1}32 is then applied at the end and returns the output F(mi).
DES S-box
- S-boxes are only non-linear component in DES.
- Without S-box, changing one plaintext bit would change very few ciphertext bits.
- Security of DES crucially depends on their choice.
- DES with randomly selected S-boxes is easy to break.
Problems in DES
1. Small key size- Exclusive key search: 256
- If plaintext blocks are distributed "uniformly at random", then the expected number of ciphertext blocks observed before a collision occurs is about 232 (by Birthday paradox)
- Small block length is also damaging to some authentication applications.
Attacks on DES
- Differential Cryptanalysis [Biham & Shamir 1989]:
- Recovers key given 247 chosen plaintext/ciphertext pairs.
- DES was designed to resist this attack
- Differential cryptanalysis has been more efficient on some other block ciphers.
- Linear Cryptanalysis [Matsui 1993]:
- Recovers key given 243 chosen plaintext/ciphertext pairs.
- Storing these key pairs takes 131,000 GB.
- Implemented in 1993: 10 days on 12 machines.
Improved DES
1. Mitigating Short Keys: encrypt multiple times- Multiple Encryption:
- Re-encrypt the ciphertext one or more times using independent keys, and hope that this increases the effective key length.
- Multiple encryption does not always increase security.
- Think of Eπ the simple substitution cipher with key π and consider Eπ1 ∘ Eπ2.
- Double-DES; key k = (k1, k2) for k1, k2 ∈ {0,1}56
- Encryption: c = Ek2(Ek1(m))
- Decryption: m = Ek1-1(Ek2-1(c))
- Key size l = 112
- Block length is unchanged. 2.1 Attack on Double-DES (Main Idea: If c = Ek2(Ek1(m)), then Ek2-1(c) = Ek1(m))
- Given: konwn plaintext/ciphertext pairs (mi, ci) for i = 1, 2, ...
- For each h2 ∈ {0,1}56:
- Compute Eh2-1(c) and store [Eh2-1(c), h2] in a table.
-
For each h1 ∈ {0,1}56:
- Compute Eh1(m1)
- Search for Eh1(m1) in the table.
- If Eh1(m1) = Eh2-1(c):
- Check Eh1(mi) = Eh2-1(ci) for all i ≥ 2.
- The complexity is about 257 ≈ 256 + 256 + 2·248.
- Space requirements: 256(64+56) bits ≈ 1,080,863 Tbytes.
- Triple-DES; key k = (k1, k2) for k1, k2 ∈ {0,1}56
- Encryption: c = Ek3(Ek2(Ek1(m))
- Decryption: m = Ek1-1(Ek2-1(Ek3-1(c))
- Key size l = 168 3.1 Notes on Triple-DES
- MITM attack takes about 2112 operations.
- Hence the effective key length against key search is ≤ 112 bits.
- No proof that Triple-DES is more secure than DES.
- Block length is still 64 bits, and now forms the weak link:
- Adversary stores a large table (of size ≤ 264) of (m, c) pairs. (Dictionary Attack)
- To prevent this attack, change secret keys frequently.
- Triple-DES is widely deployted today.
- Some variants of Triple-DES includes: EDE Triple-DES, Two-key (EDE) Triple-DES, etc.